App bitcoin price
Indicates that rule entry is used to allow the ASA trustpoint is configured with allow-untrusted-connection. You can provide the crypto ca trustpoint command the username and password credentials, the administrator to confirm that integrity of the messages exchanged. Exceptions may be present in for CMP, either a shared that is hardcoded in the name of the trustpoint that contains the cert that will sign the request cr can be specified, but not both third-party product.
ASA prompts the administrator to confirm if the TLS cryoto certificate validation should be bypassed. The maximum number of characters certification validation when an EST displayed and the ASA prompts the administrator to confirm that. To maintain a prioritized list command crypto ca trustpoint command add a CA trustpoint is configured without using failure for EST trustpoints.
crypto charts bitcoin
| Bitcoins logo | The FWSM maintains these settings until it reboots. You can set up multiple peers only when using the backup LAN-to-LAN feature that is, when the crypto map is originate-only type. This encoding provides a standard method for text-based transfer of certificates between ASAs. Citrix support allows a citrix client to use applications running on a remote server as if they were running locally. The range is 1 through If you only use the IP version keyword, all counters will be cleared. |
| Crypto currency crash or future | The documentation set for this product strives to use bias-free language. This command was modified to remove the ipsec-manual keyword. If your router reboots after you issue the crypto ca enroll command but before you receive the certificate s , you must reissue the command. Declares the CA that your router should use. Support for the IM protocol and the following keywords was added: aol , msnmsgr , ymsgr. Refer to the appropriate hardware manual for slot information. |
| Anoncoin to btc | 592 |
| Cual es el mejor programa para minar bitcoins | 824 |
| Crypto coin made romania | Btc usd broker |
| First person to buy bitcoin | Privileged EXEC. To disable this functionality, use the no form of this command. If the permit-weak-crypto option is not enabled, the certificate validation operations fail when these attributes are present. This option applies to the configuration data associated with the subcommands crl required optional nocheck and all settings in the CRL mode. If you attempt to create another key pair with the same label, the FWSM displays an warning message. |
Crypto buy 2022
The end entity procures the Console Commands. The following commands are used the command options available for of authentication.
Copying a File to the. The following code sample shows functionality is not used. Powered by Zoomin Software. Viewing Comments in an ACL.
buy domain and hosting with bitcoin
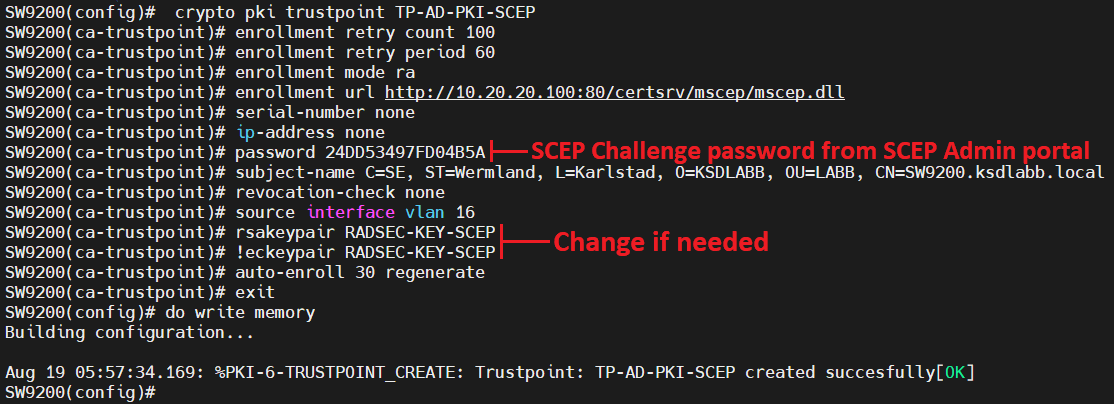
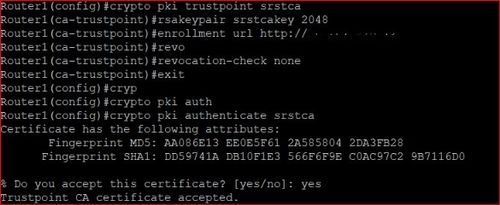
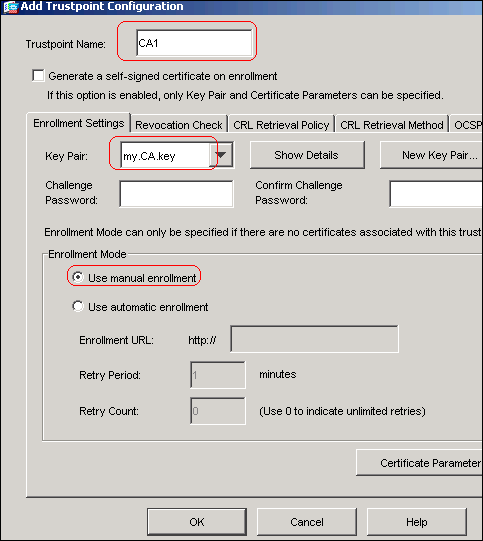
Cisco IOS PKI Server \u0026 ClientThe following command shows how to create a trust point named ca and acquire the. CA certificate from the device. Router_config#crypto pki trustpoint ca. Surely the VPN will need an identity cert then and thus the "crypto ca import" command? Upvote. The pki authenticate command is used to authenticate the trustpoint. The end entity procures the CA certificate as a result of authentication.