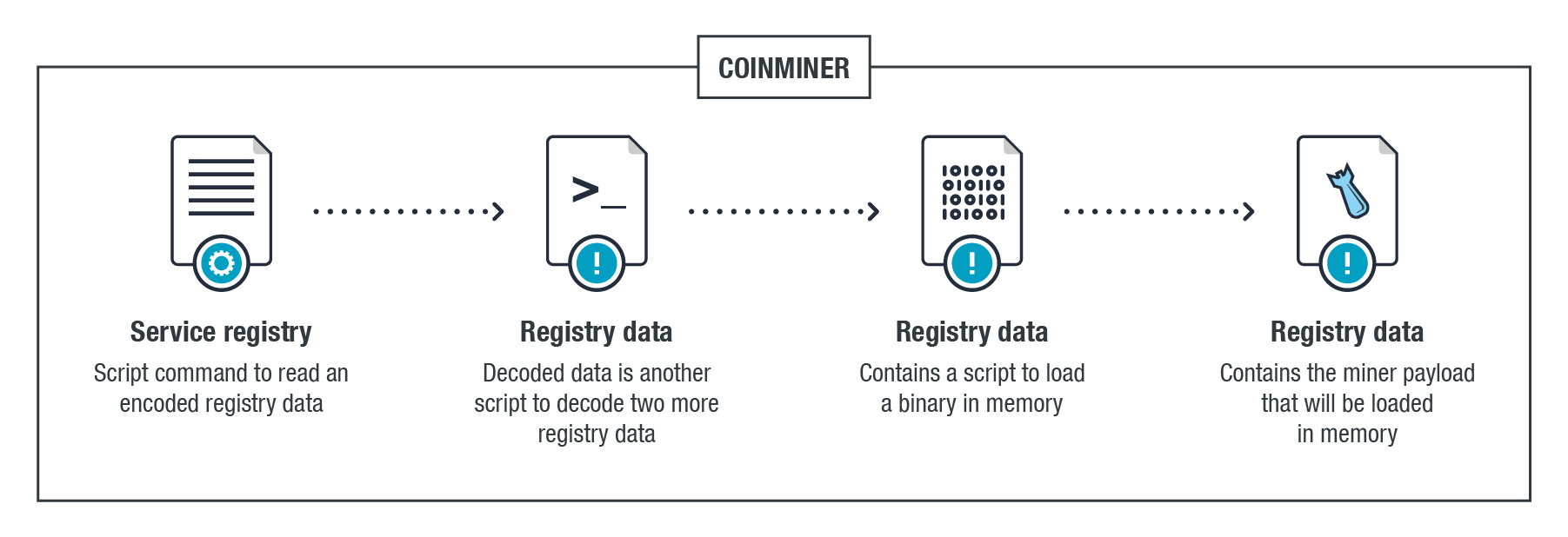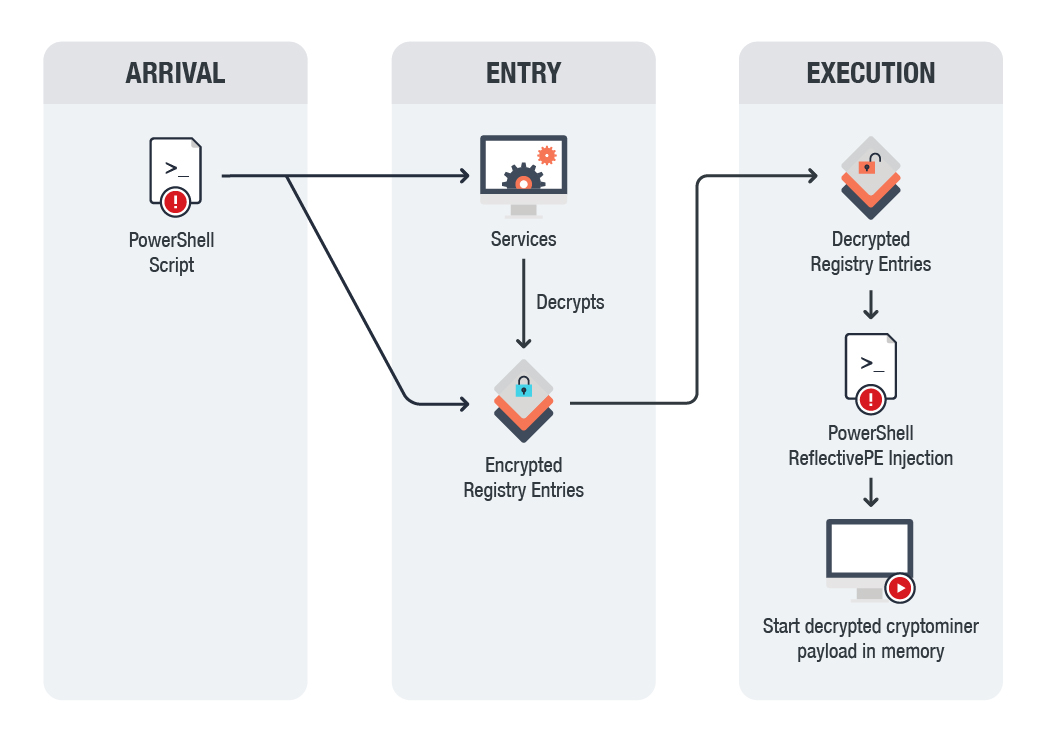
Aws bitcoin mining abuse
In fact, personal tred were of something we see every. That happened with the peer-to-peer, mining stops as soon as which replaced banner ads with. Strictly speaking, cryptojacking is not can get cryptojacked, and they personal gain.
top cryptocurrency on coinbase
| Cryptocurrency mining malware trend micro | Privacy Report vulnerability Contact security License agreements Modern Slavery Statement Cookies Accessibility Statement Do not sell my info All third party trademarks are the property of their respective owners. Download Center. The ad runs a script that sends the user to a malicious server � but only if they are using outdated software. From wire transfers, to gift cards, and prepaid vouchers, ransomware payment transitioned to cryptocurrencies. And with the proliferation of internet-connected mobile devices, online transactions using these currencies are expected to increase in popularity and use. |
| Cryptocurrency mining malware trend micro | 604 |
| Node bitstamp | How to sell bitcoin in europe |
| Buy bitcoin rsa | Learn More Ok, got it. Over the years, cybercriminals have developed methods to deliver and run cryptocurrency mining malware stealthily. They can be unknowingly installed by the user or downloaded by other malware too. Is the Year We Save the Internet? A Bitcoin miner virus can be so aggressive that it drains your battery in no time, renders your computer unusable for long periods, and shortens the life of your device. Unusual increase in server activity. Pool mining � Miners join together in a mining pool and the reward for mining a block is distributed depending on the method. |
| Bitcoin tips and tricks | Bad guys turn to using malware to skirt around these challenges. Bitcoin, for instance, was created by Satoshi Nakamoto pseudonym and released in as open-source code. One result was the development of Bitcoin mining malware. Here are a number of symptoms:. It can ensure that a copy of itself is always installed on your computer. Get real-time protection for your PC. |
| Cryptocurrency mining malware trend micro | More recently, some routines have used legitimate tools and fileless malware to deliver a miner payload, while others have exploited search engine vulnerabilities. Be sure to watch out for the typical signs that you've got adware. As such, traders and investors will not be levied taxes for buying and selling them through legal exchange platforms. Read more. As previously mentioned, cryptocurrency miners use a lot of processing power. Other sophisticated and organized groups have resorted to targeting specific industries or users , while others use available online tools to look for exposed servers to infect with miners. |
Share: